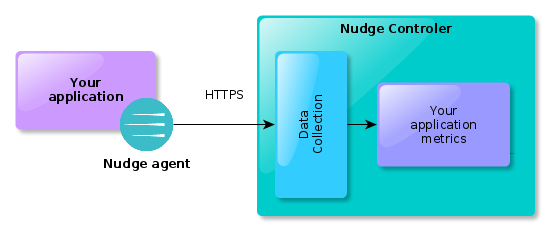
Nudge APM gather metrics about your application and its environment by using a Nudge agent. This agent depends on the way your application is built.
Metrics are sent by using the encrypted HTTPS protocol (by default) towards the Nudge controler that will store and analyze them.
Install
- Log in to the PH-Nudge APM user interface
- From the main dashboard, create your app by clicking on the “New application” button
- Choose the type of environment (prod/not prod) and accept the terms of use
- Fill the application creation form
- Next steps depends on the technology of your application:
Security
This document describes the tools and procedures that we implement to provide you reliable and secure usage.
Securing network traffic
Network exchanges between agents and the platform use HTTPS and are therefore encrypted.
It is possible to complement this by implementing a VPN.
Network streams
The agents send the information collected in a very compact format developed by Google called protocol buffer.
We provide an unpacking tool to facilitate the audit of these flows. Please contact us if you want more information about this topic at support@atakama-technologies.com.
No transfer of business data
The data collected by the probe (HTTP, SQL requests…) is anonymized before being sent to the Nudge APM platform.
For example, an SQL query appears like that from the Nudge APM point of view :
SELECT * from CUSTOMER where NAME = 'customer name', becomes SELECT * from CUSTOMER where NAME =?
In some cases (notably for transaction qualification requirements) it is possible to define an HTTP parameter list in the probe configuration file that may exceptionally be sent to the Nudge APM platform.
Management of user rights
Nudge APM relies on an ORBAC (Organisation Role Based Access Control) user rights management system.
A user may thus have specific rights on each application (administrator on Application A and guest on application B, for example).
Audit trail
The information related to your account is provided with an audit trail. It is thus possible to trace the changes in parameters such as adding or (modifying a user’s rights, the creation / modification of filters …).
Redundant architecture
The technical components of our architecture on our servers use redundancy.
This also applies to the data we receive and analyze.
We rely on a NoSQL type architecture used by major web players.



